Basic cracking a program using Cutter

Install Cutter from this link Cutter Radare.
Create a simple program called
vulnerable_license.c.#include <string.h> #include <stdio.h> int main(int argc, char *argv[]) { if(argc==2) { printf("Checking License: %s\n", argv[1]); if(strcmp(argv[1], "AABB-CCDD-20-OK")==0) { printf("Access Granted!\n"); } else { printf("WRONG!\n"); } } else { printf("Usage: <key>\n"); } return 0; }This program basically check the correct license to get the access of the program.
Then, compile the program using default
gccoption.gcc vulnerable_license.c -o vulnerable_license# Example: if your input is "AABB-CCDD-20-OK" you get the access, else you get "WRONG!". $ ./vulnerable_license AABB-CCDD-21-MM Checking License: AABB-CCDD-21-MM WRONG! $ ./vulnerable_license AABB-CCDD-20-OK Checking License: AABB-CCDD-20-OK Access Granted!Open your
Cutterapp and load the compiled file before and make sure to checked the write mode.
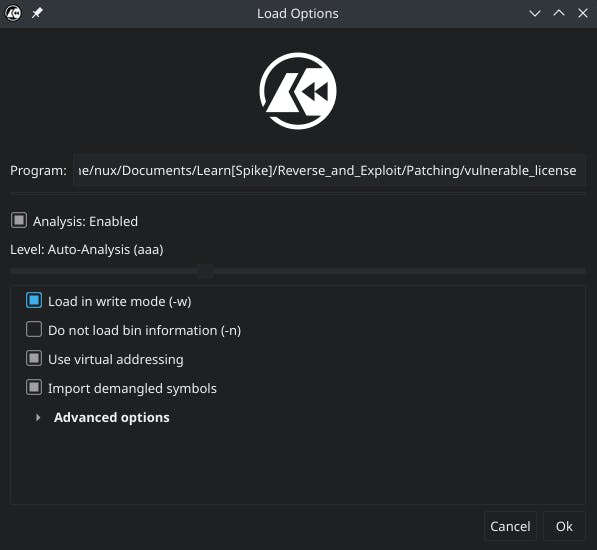
You will look something like this.
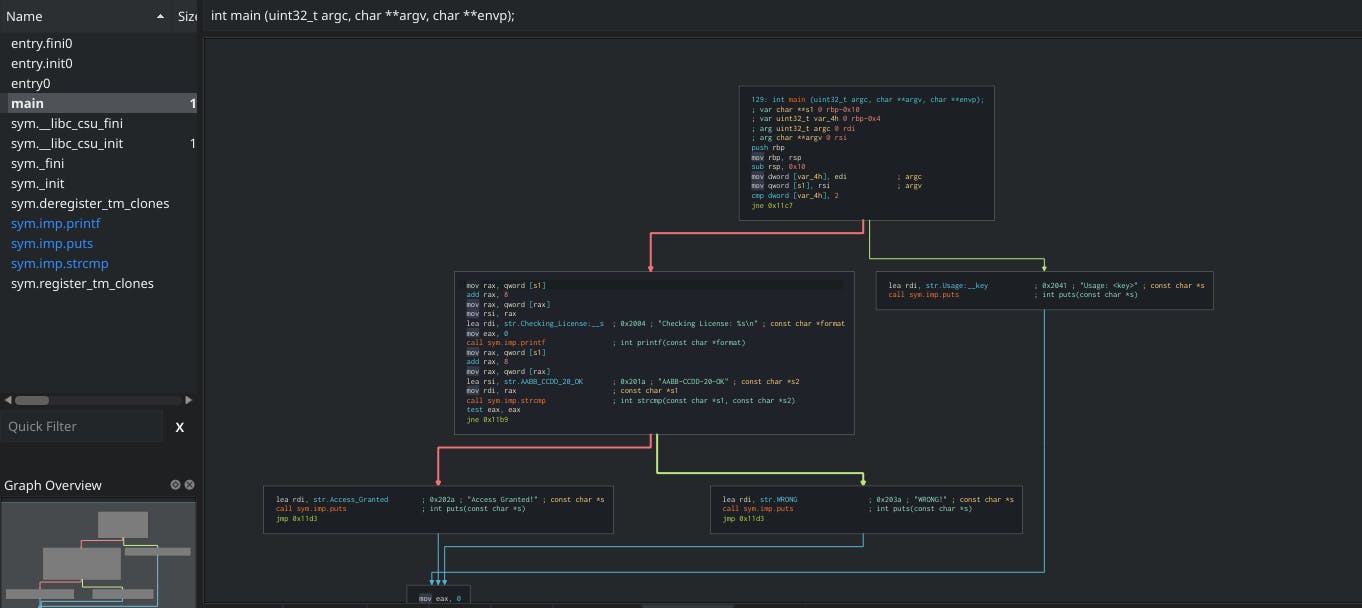
We interested in
mainfunction, because we see there's a checker, so we need to bypass the checker by changing the flow of the program.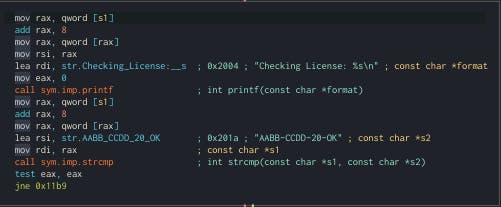
From the picture above, there's some mechanism to change the flow by using
reverse jumpin Cutter. We tend to change the flow of resulttest eax eax, by default if the result notzeroorthe string is not sameit will jump to "WRONG!" so we need to reverse the logic, by allowing thewrong stringto grant the access.You need to click the
jne 0x11b9in my case, other computers maybe different.Edit -> Reverse Jump. The new change will similar like this.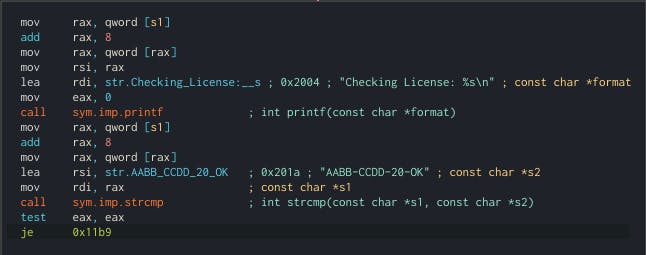
By runtime the flow of the program is changed.
Save the changes and try to run the program again.
$ ./vulnerable_license AABB-CCDD-21-MM Checking License: AABB-CCDD-21-MM Access Granted! $ ./vulnerable_license AABB-CCDD-20-OK Checking License: AABB-CCDD-20-OK WRONG!
Source: Patch Binaries with Cutter
